Understanding Internet Protocols
In the previous article in this series, we explored the fundamentals of internet protocols. Now, let's delve deeper into the transition from unsecure protocols to secure protocols, focusing on securing the transport and application layers in the OSI model.
The Role of Transmission Control Protocol (TCP)
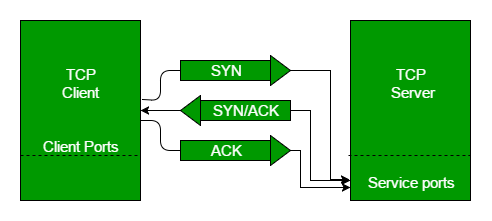
The Transmission Control Protocol (TCP) is a crucial transport protocol responsible for ensuring the reliable transmission of data. It establishes connections with recipients, organizes data packets, and confirms the receipt of each packet. TCP is known for its reliability, although it may not be the fastest protocol due to its robust error-checking mechanisms.
In conjunction with the Internet Protocol (IP), TCP forms the TCP/IP suite. While TCP and IP were initially designed to work together, other transport protocols can also be used with IP.
One notable aspect of TCP is its three-way handshake method for connection establishment. This ensures a secure and reliable communication channel between sender and receiver.
Ensuring Data Security with SSL/TLS
Security is a critical concern in the transportation layer. To address this, Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols are utilized to encrypt data transmitted over the network.
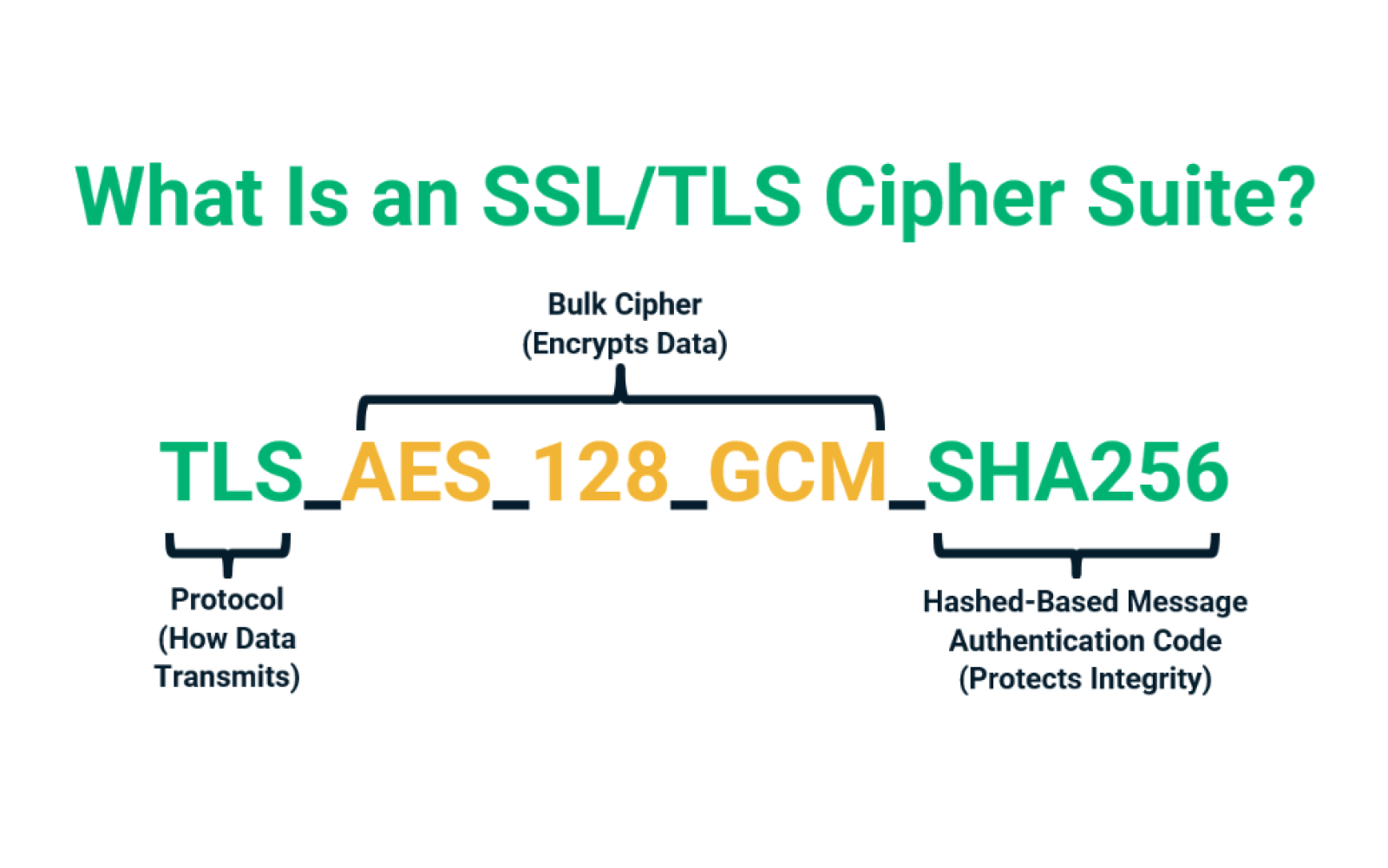
SSL and TLS employ advanced encryption algorithms, digital certificates, and asymmetric keys to secure data transmissions. Additionally, TLS 1.3 has enhanced security features, such as support for the Diffie-Hellman key exchange algorithm.
Furthermore, SSL/TLS protocols utilize symmetric keys for efficient encryption and decryption of data. By implementing these protocols, data integrity and confidentiality are maintained during communication.
Enhancing Security with QUIC and SSH
QUIC (Quick UDP Internet Connections) is a new transport protocol designed to enhance security and speed by leveraging UDP. QUIC aims to replace TCP and TLS for improved web connectivity.
On the other hand, Secure Shell (SSH) protocol provides a secure means of connecting to remote systems. SSH employs encryption and authentication mechanisms, making it a preferred choice over Telnet for secure remote access.
Securing File Transfers and DNS with FTPS, SFTP, and DNSSEC
File Transfer Protocol (FTP) and its secure variants, FTPS and SFTP, ensure secure file transfers over the network. FTPS and SFTP use SSL/TLS and SSH protocols, respectively, to encrypt data transmissions.
Domain Name System Security Extensions (DNSSEC) enhance the security of the Domain Name System (DNS) by validating domain records using cryptographic keys. DNSSEC helps prevent DNS-related attacks and ensures the integrity of domain information.
Conclusion
As we have explored various internet protocols and their security implications, it is evident that utilizing secure protocols at every layer is essential for maintaining data security. By implementing SSL/TLS, SSH, DNSSEC, and other secure protocols, organizations can ensure the confidentiality and integrity of their data transmissions.










