'I Break Into Buildings And Pretend To Be The Bad Guy' • The Insider's Perspective
A hacker recently shared a fascinating account of breaking into a "very big city" building without any keys and successfully infiltrating both the physical space and the corporate Wi-Fi network. Despite the lack of breaking in, the hacker managed to steal sensitive data effortlessly.
The hacker, Alethe Denis, a senior security consultant at Bishop Fox, specializes in physical security assessments. Describing her work as "breaking into buildings," Denis also boasts accolades such as winning a DEF CON Social Engineering Capture the Flag competition and earning a spot in the hacker summer camp Black Badge Hall of Fame.

Social Engineering Tactics
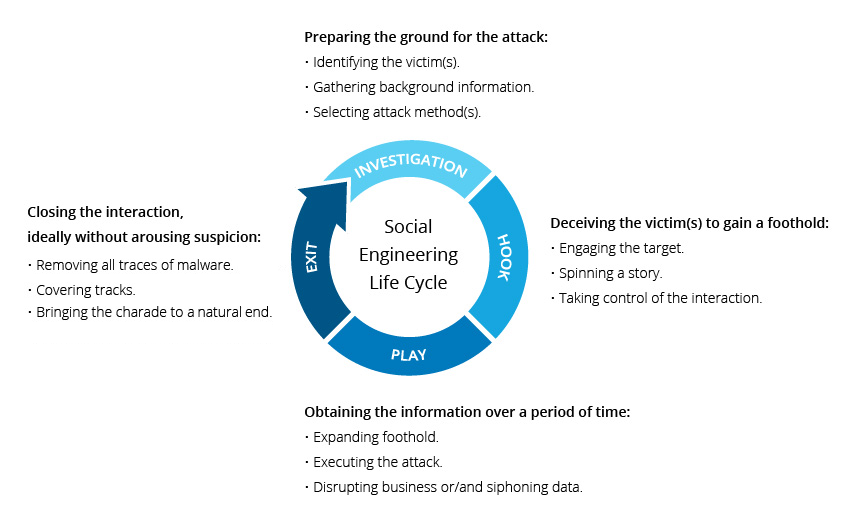
Denis's work involves intricate social engineering attacks where she and her team impersonate individuals like former employees or vendors to gain access to corporate networks. By leveraging elaborate pretexts and creating compelling characters, they aim to extract valuable information that only high-level executives should have access to.
One of Denis's notable engagements involved posing as IT contractors to conduct a site survey at a software provider's facility. Despite meticulous preparation, including creating a fake vendor company, the team faced a setback when a security manager recognized their ruse and thwarted their attempted break-in.
The Power of Human Interaction
Denis emphasizes that despite advancements in AI-assisted social engineering tools and deepfakes, human conversations remain the primary and most effective method for cybercriminals. By triggering emotional responses through tailored phishing emails and exploiting vulnerabilities, attackers can gain unauthorized access to systems.

Defense Strategies
Detecting and thwarting social engineering attacks requires vigilance and skepticism. Denis recommends asking questions and maintaining a cautious approach to unsolicited emails or phone calls. By proactively engaging and verifying the legitimacy of requests, individuals can minimize the risk of falling victim to such attacks.
While the allure of AI-driven tactics exists, Denis stresses that traditional social engineering methods, such as voice phishing, remain prevalent due to their success in manipulating human behavior. By understanding and recognizing these tactics, individuals and organizations can bolster their defenses against cyber threats.
As technology evolves, staying informed and proactive in safeguarding sensitive information is crucial in mitigating the impact of social engineering attacks.
Source link









