A Billion Devices at Risk: Uncovering the ESP32 Bluetooth Chip
As a tech reviewer, I’m always on the lookout for the latest tech breakthroughs—and the potential pitfalls that come with them. A recent report from cybersecurity researchers at Tarlogic has sent shockwaves through the tech world, revealing a serious security flaw in a Bluetooth chip that powers over a billion devices. Known as the ESP32, this chip from Chinese manufacturer Espressif is a staple in everything from smartphones and laptops to the ever-growing array of Internet of Things (IoT) gadgets like smart locks and appliances. Here’s what you need to know about this discovery and what it means for your connected devices.
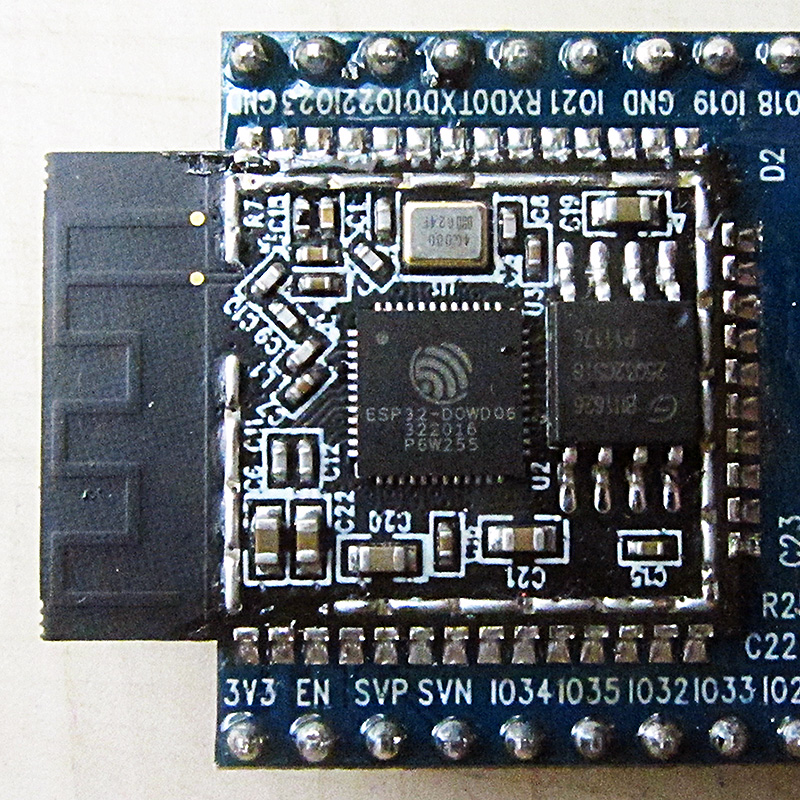
The ESP32: A Dual WiFi and Bluetooth Microcontroller
The ESP32 is a microcontroller celebrated for its dual WiFi and Bluetooth capabilities, making it a go-to choice for manufacturers. Priced at just $2 per unit, it’s no surprise that Espressif has sold over a billion of these chips since its launch. But affordability, it seems, might have a hidden cost. Tarlogic’s researchers uncovered 29 undocumented commands embedded in the ESP32—secret functionalities that Espressif never disclosed. These commands aren’t just Easter eggs; they’re potential backdoors that hackers could exploit, as detailed in BleepingComputer’s coverage.
Security Risks and Implications
Using these hidden commands, a malicious actor could impersonate a trusted device—think your wireless keyboard, headset, or even a smartwatch. Once the hacker’s device is recognized as “trusted” by your gadget, they could connect to it, siphon off sensitive data, or even maintain a persistent connection to spy on you. Imagine your smart thermostat or medical device being silently compromised—all because of a chip that’s cheaper than a cup of coffee.
Uncovering the Vulnerabilities
Tarlogic didn’t stumble upon this by accident. They developed a custom Bluetooth driver tool, called BluetoothUSB, to dig into the ESP32’s inner workings, a move that paid off by exposing these 29 vulnerabilities. This tool, which Tarlogic describes as a breakthrough for Bluetooth security research, could become a game-changer for uncovering similar flaws in other widely used components. For now, though, the spotlight is on the ESP32, and the findings are tracked under the identifier CVE-2021-32504.










