Using a Pluggable Authentication Module for Verifying User Identities in Ubuntu and Other Linux Flavours
Pluggable authentication modules (PAM) play a crucial role in the authentication process by separating authentication tasks from applications. In Linux environments like Ubuntu, PAM helps in user identification across various interfaces, such as the user interface, terminal, and other access points. Applications like login, gdm, sshd, and ftpd often need to verify user identities using different methods like passwords, LDAP, Kerberos, fingerprints, or certificates.
Implementing new authentication methods for each application can be inefficient and error-prone. PAM addresses this issue by providing libraries that applications can utilize for authentication, allowing authentication experts to handle the details. Its modular and pluggable design enables different applications to apply distinct authentication tests without the need for custom implementations.
Creating an API-Based Login Mechanism with Custom PAM Module
Building a login mechanism that is API-based involves leveraging a custom PAM module to handle user authentication. This PAM module communicates with an API server for validation and authentication based on the server's response. By following the steps outlined below, you can implement this custom login scheme:
- Prompt the user to enter their password or key.
- Send the authentication request to the API server for validation.
- Receive the response from the server and verify the authentication details on the host PC.
The source repository contains the necessary code for the server that processes API requests and the custom PAM module. Once you have built the project, the output will be stored in the lib directory. Install Node.js and npm on the server hosting the API to ensure its functionality.
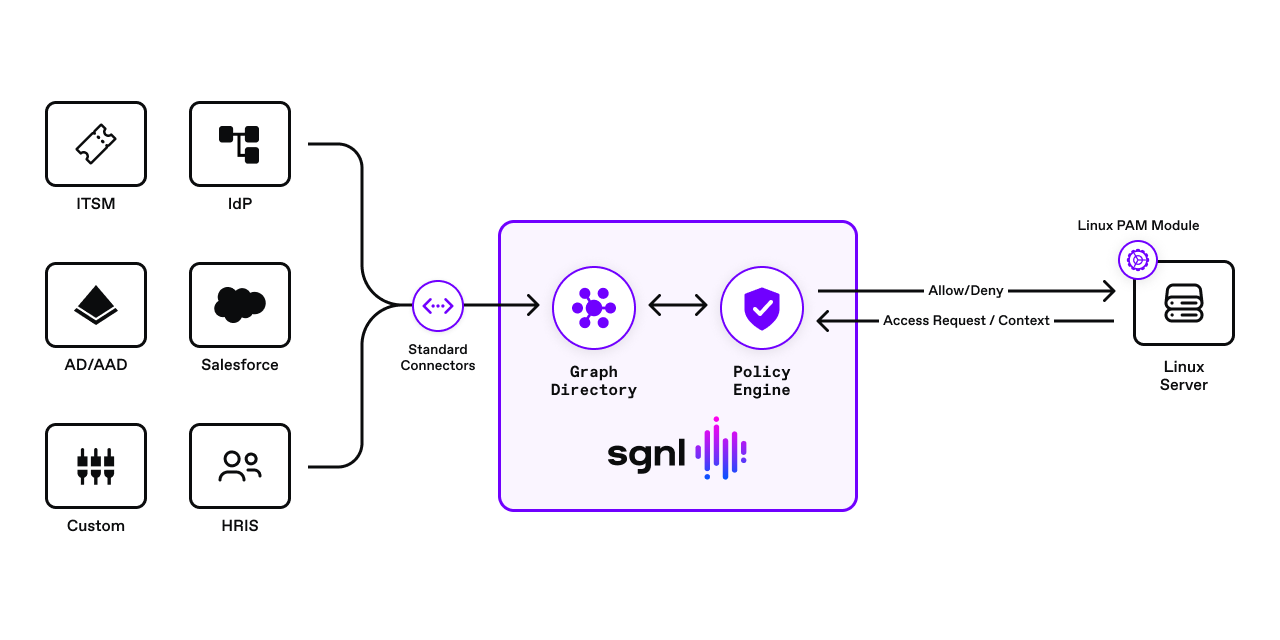
To build and install the PAM module, follow these steps:
- Install dependencies for building and running the PAM module.
- Modify the build configuration settings in the INI file (mypam-cfg.ini) to suit your requirements, including the server URL and login replacement settings.
- Build the module using the provided command.
- Install the module on the host PC to enable login functionalities based on the configuration.
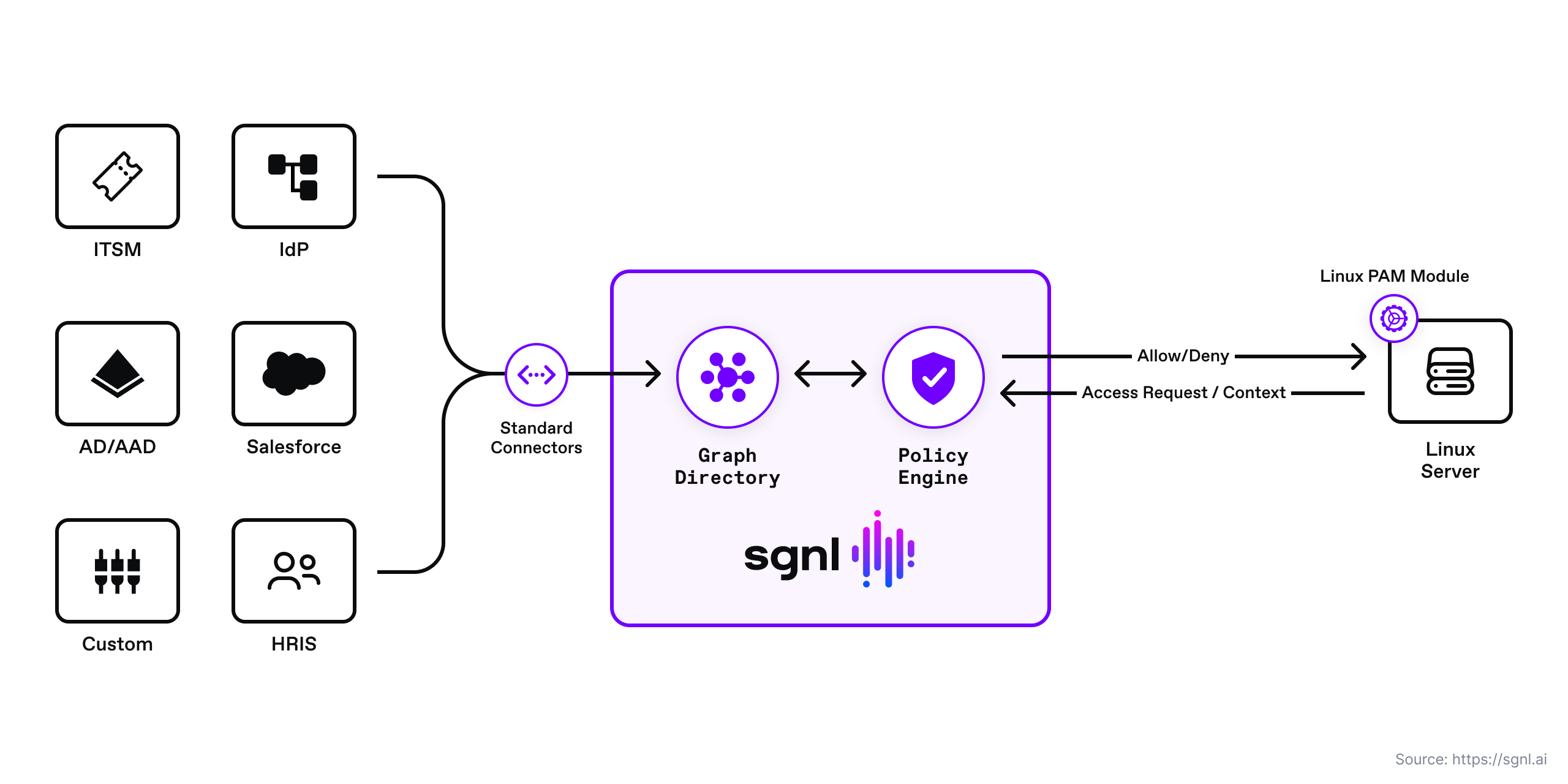
To test the setup, ensure the server is running the appropriate script, establish communication between the host PC and the server, and configure users in GitHub for authentication purposes. You can further customize the PAM module for different authentication scenarios by exploring the code available on GitHub.










