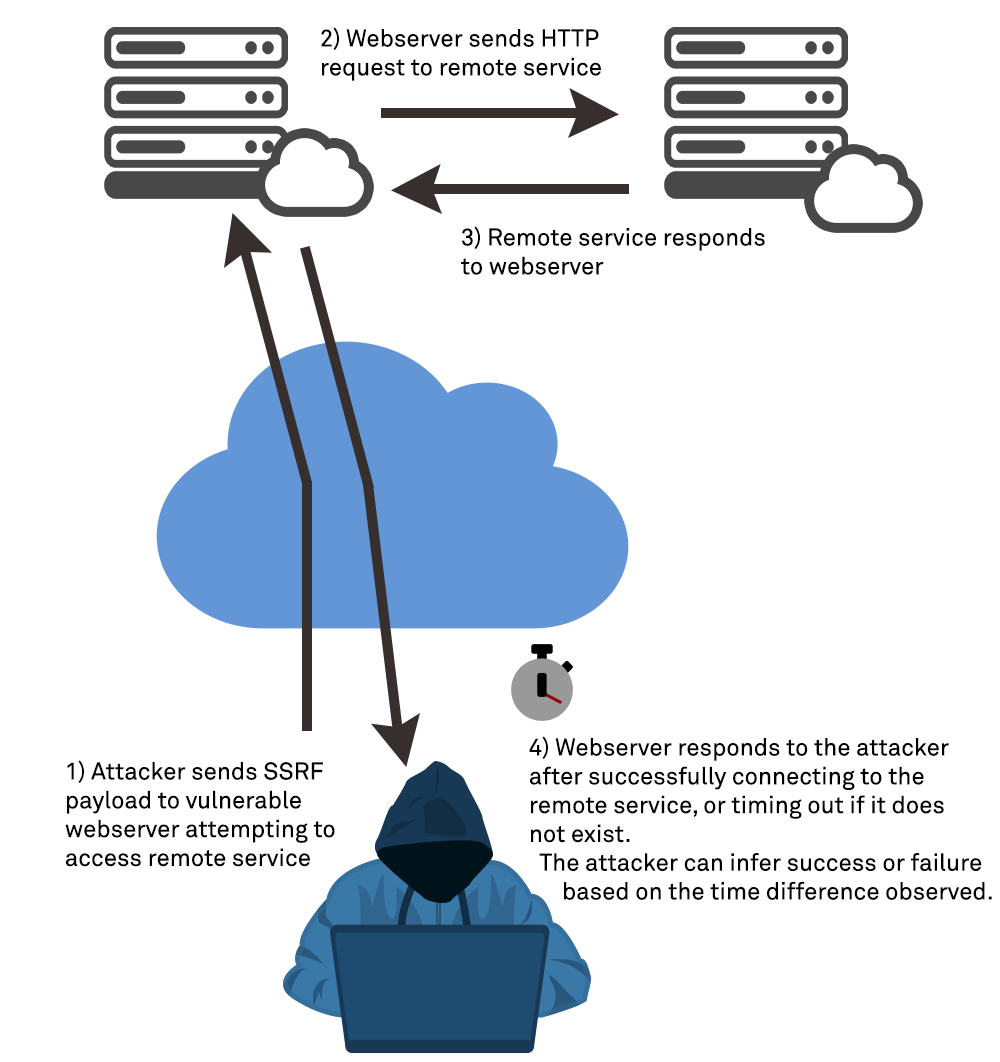
ChatGPT SSRF bug quickly becomes a favorite attack vector
Recently, there has been a surge in cyberattacks targeting various organizations and institutions. One particularly popular method among hackers has been the exploitation of Server-Side Request Forgery (SSRF) vulnerabilities. This type of vulnerability allows attackers to send crafted requests from the server to other resources on the internet, often leading to unauthorized access or data leaks.
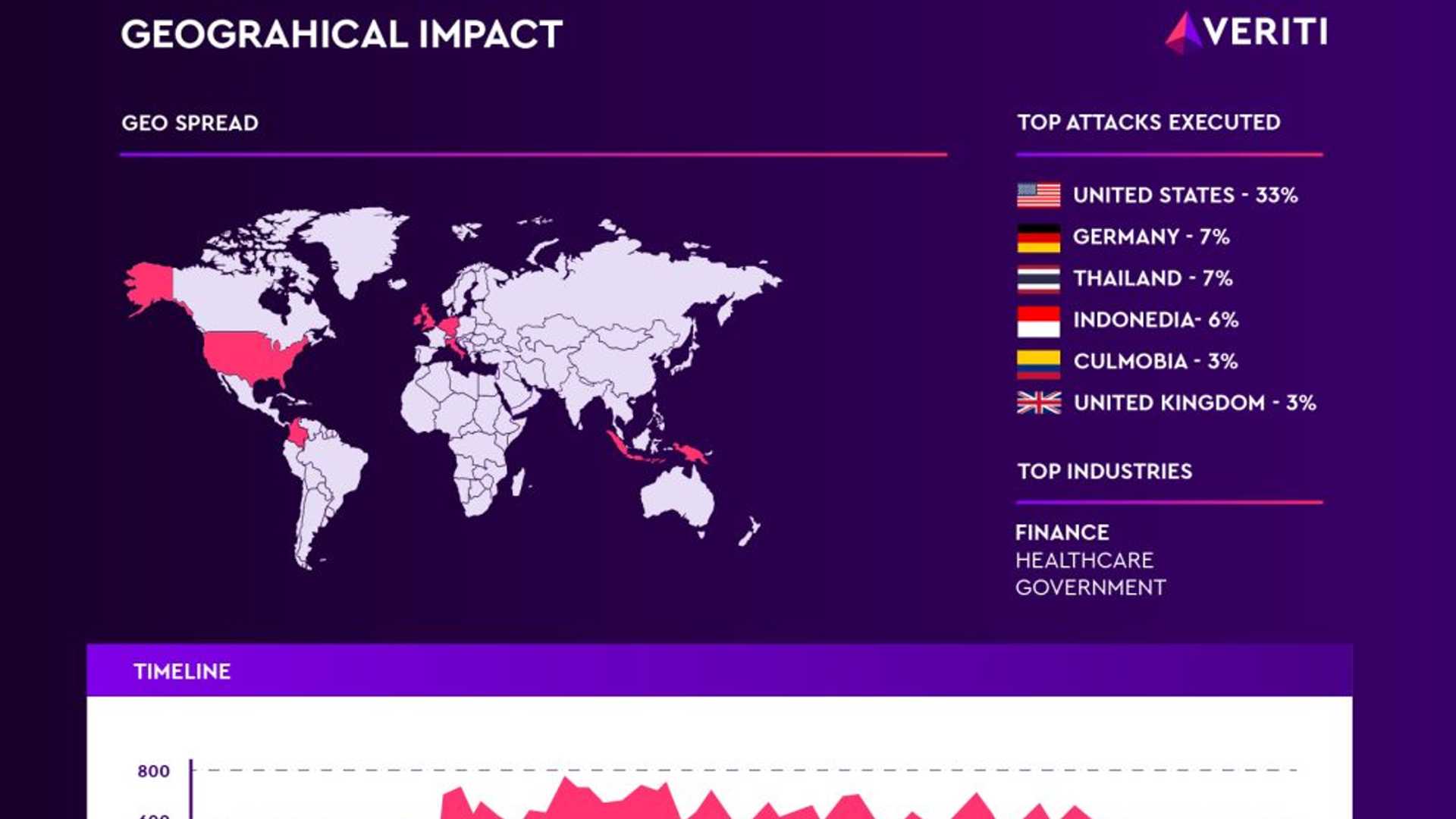
Recent Cybersecurity Incidents
Canada’s second-largest airline, WestJet, is currently dealing with a cyberattack, highlighting the growing threat posed by malicious actors. Similarly, Palo Alto Networks recently addressed several privilege escalation flaws in their systems, underscoring the importance of regularly updating security measures to prevent such incidents.
Impact on Organizations
These cyberattacks have had significant consequences, such as bread shortages caused by an attack on United Natural Foods. Furthermore, Paraguay's data breach involving millions of citizen records highlights the far-reaching implications of such security breaches.
Response and Mitigation
In response to these threats, organizations are taking proactive measures. Google swiftly addressed a flaw that could potentially expose users' phone numbers, emphasizing the need for prompt action to mitigate risks. Additionally, U.S. CISA has been updating its Known Exploited Vulnerabilities catalog to help organizations stay informed and protected against emerging threats.

Conclusion
As cybersecurity threats continue to evolve, it is crucial for organizations to remain vigilant and implement robust security measures. The prevalence of SSRF vulnerabilities as a favored attack vector highlights the importance of addressing these issues promptly to safeguard sensitive data and maintain the integrity of digital systems.